09.03.2021 | Thomas Kessler
2-factor Authentication of Healthcare Professionals

Two-factor authentication of users should become a matter of course when accessing cloud services in the healthcare sector. For this to succeed, hospitals and care homes need an electronic equivalent to an ID card.
Passwords are the Achilles heel of IT security
When logging in with a user name and password, users prove their identity by revealing a secret, namely their personal password. It is well known that a shared secret is no longer a secret. This fundamental weakness of passwords repeatedly leads to successful attacks on our IT systems and is one of the reasons why identity theft is one of the top ten IT security risks.
It has long been known that such attacks can be countered with so-called 2-factor authentication (hereafter abbreviated to “2FA”), as is commonly used in e-banking, for example. We use the term 2FA to describe procedures that combine a “having” factor with a “knowing” or “being” factor. The “having” factor is always required, which can be hardware (a smartcard, SIM card or other token) or software (for example, an authenticator app). The “knowing” factor is usually a password that is managed and checked centrally on a server or decentrally on a personal device; the latter is also known as a PIN. Finally, the “being” factor is an individual physical feature such as a fingerprint or facial image.
Where is 2-factor authentication appropriate?
The risk of identity theft is assessed by multiplying the probability of occurrence of a loss event by its scope. The scope is naturally high in the healthcare sector, as in many cases it involves access to particularly sensitive personal data.
The probability of occurrence is particularly high if an IT system is exposed on the Internet and is therefore accessible to the whole world. This applies to most remote access solutions, for example, which is why two-factor authentication is highly recommended for this use case. However, it also applies to many cloud applications such as the electronic patient dossier (EPD), where 2FA is therefore required by law for good reason.
The situation is less clear when using IT systems within an organization. Because it is becoming increasingly difficult to isolate internal IT systems from the Internet, 2-factor authentication should also be sought in the medium term when logging in to the workplace and internal applications. However, the operational requirements (keyword “station PC”) can make such a solution very demanding and time-consuming.
How can 2-factor authentication be achieved?
The introduction of 2FA individually for each IT system should be avoided at all costs so that users are not flooded with a flood of additional “login factors”: An overarching infrastructure is needed! There are two strategic approaches for this:
- In the “2FA on the end device” variant, 2-factor authentication is already carried out when logging in at the workplace, typically using a smartcard and PIN. The user’s identity authenticated with two factors is then passed on to all connected IT systems via infrastructure components such as the Active Directory (single sign-on).
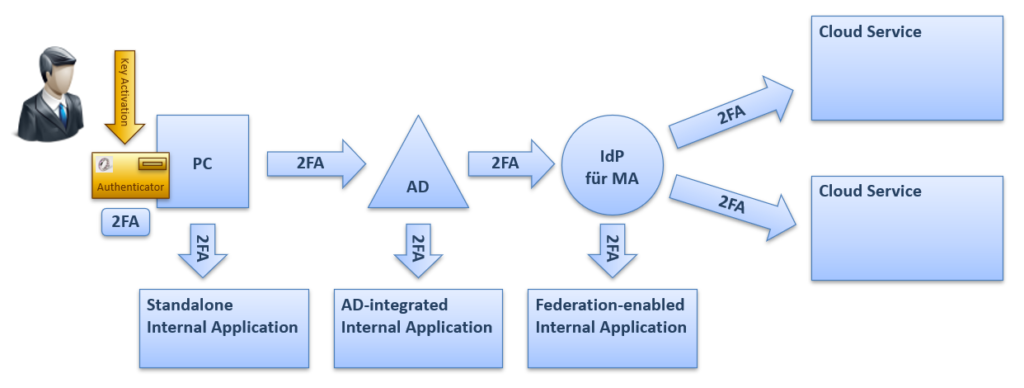
- With the “2FA at IdP” variant, the user first logs in to the workplace with their password or a biometric feature. The second factor, often the possession of an authenticator app, is checked at a later stage at a so-called identity provider (IdP).
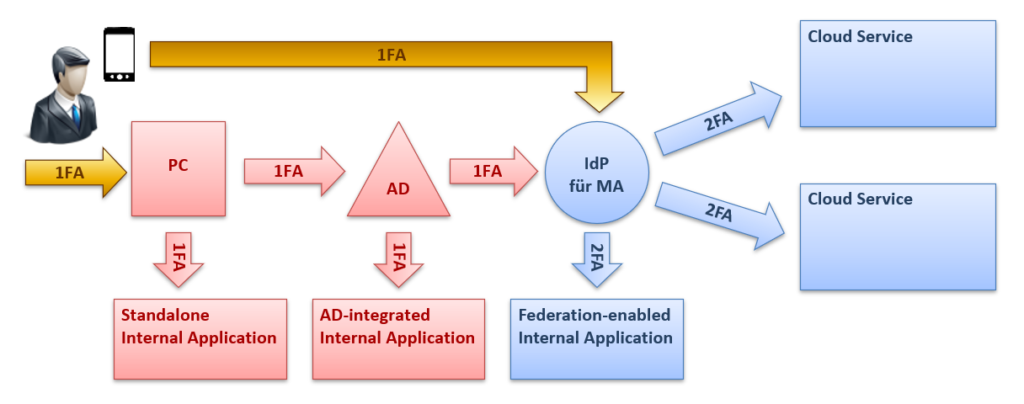
The operational implementation of the second variant is usually much simpler. However, it also offers a lower security benefit because only modern IT systems can be connected to an IdP.
The thing with the digital ID card
For the efficient implementation of 2-factor authentication, hospitals and care homes need the digital equivalent of an ID card: a digital ID card that is used for 2FA. This is issued by an internal specialist department (e.g. HR) and contains information such as the personnel number or organizational affiliation that is typically required when using IT systems in a professional context.
The digital ID card is based on the same technology as the digital ID card for private individuals, which is currently the subject of lively debate in connection with the E-ID Act. However, the significant differences between an ID card and a passport in terms of responsibilities, administrative processes and use cases also exist in the digital world and must be taken into account in a 2FA implementation project.
Note: This article was also published in the magazine Arzt Spital Pflege | 1/2021.

