30.06.2018 | Michael Roth
Data Protection vs. Information Security?

The issue of data protection always plays a role in the design and operation of information security - not always to the delight of business managers.
Information security consulting usually deals with topics such as cybersecurity, identity and access management or information security management systems. These areas are usually located in the client’s IT or business units and are intended to protect the company’s information from all possible breaches.
Integral approach
Data protection as a discipline of civil law, on the other hand, aims to protect the persons associated with the information; it is rarely the catalyst for security projects and is at best considered as a framework condition. The objectives of the two fields of consideration are therefore different, but overlap to a large extent. They can therefore hardly be dealt with in isolation.
As a rule, existing internal and external framework conditions of the customer must be taken into account when fulfilling the mandate. These include security strategies and guidelines such as applicable standards or classification specifications. In addition, legal requirements always apply to the processing of personal data, usually also for other company data. It is therefore imperative for all work in one of the two domains to approach the issue integra and not to disregard the requirements of the other domain. Examples of this can be found in abundance, particularly in highly regulated economic sectors such as the financial industry or healthcare.
Standards and compliance
Projects often aim to determine the status of a company’s own information security in terms of industry practice and the state of the art. Established standards, such as the ISO/IEC 27001 standard, the NIS Cybersecurity Framework or industry-specific references such as HIPAA for the healthcare sector or PCI-DSS for credit card transactions, can serve this purpose well. All of these standards also include requirements for the implementation of data protection resulting from national or other applicable law.
Conversely, data protection law also practically always includes generic information security measures (technical and organizational measures); in Swiss law, they can be found in Article 7 FADP, and in the European GDPR in Article 32. If a court has to examine the appropriateness of data protection measures, it will most likely base its determination on the aforementioned or comparable (industry) standards. Experience has shown that the same applies to more or less specific requirements of the relevant regulator.
There is therefore a high degree of interaction between factual and formal law on information security and data protection; both sources for data processing measures cannot be considered in isolation.
Cooperation instead of demarcation
In the day-to-day work of information security consultants, this interaction rarely arises by itself Information security is now widely recognized as a business enabler and is usually designed and operated seriously - also because it only has to meet internal requirements as far as possible. Data protection, on the other hand, is still regarded as a classic (legal/external) framework condition, and therefore as a brake on business.
Nevertheless, it is clear that the disciplines cannot be separated; they are mutually dependent and fulfill each other, and the underlying system can rarely be changed on one side without affecting the other. The formal linking of the two areas is correct and necessary in terms of content. A project to introduce an IAM system or legally compliant archiving in accordance with GeBüV or other retention regulations is inconceivable without an in-depth examination of the associated data protection requirements.
Project assignments should take this initial situation into account. The project setup, target definition and measurement as well as the effects of the project results must be implemented accordingly, and should be expanded if necessary. The company’s legal service, ideally the data protection officer, can provide support in this regard.
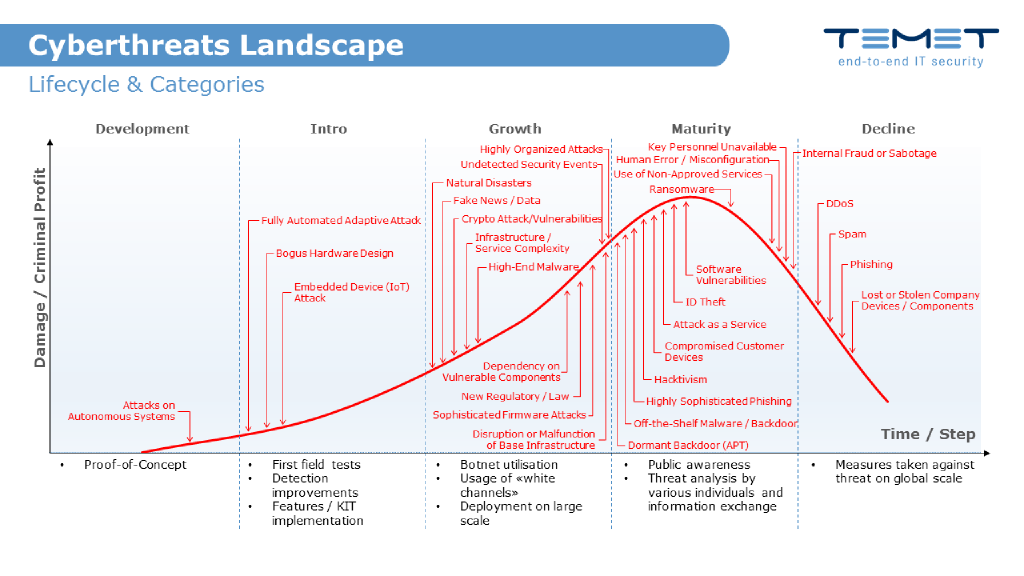
Possible threats to information security
Note: This article was also published in Wirtschaftsguide as a supplement to the Sonntagszeitung.

