18.12.2018 | André Clerc
The Agony of Choice: Android and iOS in Corporate use

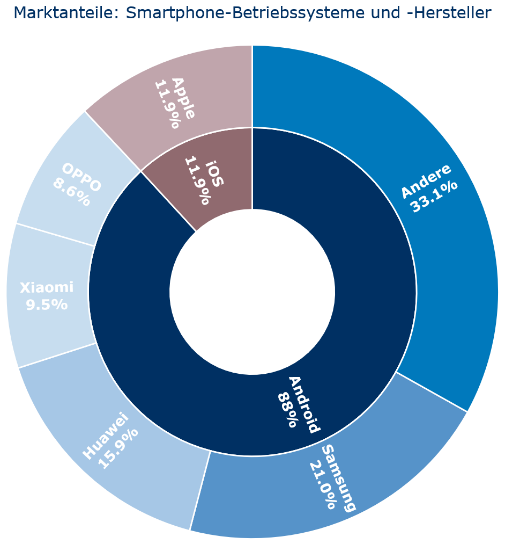
Mobile devices such as smartphones and tablets are playing an increasingly important role in both professional and private environments. In many companies, iOS devices from Apple are the standard - but why aren’t devices with the Android operating system also used? With over 88% market share, Android dominates the international market for mobile devices and the largest manufacturers such as Samsung and Huawei offer high-end smartphones comparable to Apple. In terms of security, however, Android has a reputation for being less secure than iOS. TEMET AG got to the bottom of the matter and compared the security of both operating systems in a report. The documented vulnerabilities of both operating systems since 2013 and mobile threats from the last three years were analyzed.
Number of vulnerabilities and damage potential
The chart below shows how the number of documented vulnerabilities and their average weighted damage potential have changed since 2013. The evaluation makes it clear that neither operating system is immune to vulnerabilities and that the damage potential for Android (6.9/10) and iOS (6.4/10) is currently only just below the High score (7.0-8.9/10). Looking only at the critical vulnerabilities of the latest operating systems (for which vulnerabilities are known), at least 21 critical vulnerabilities are currently reported for iOS 11.1 and at least 23 for Android 8.1. Basically, one vulnerability is enough to compromise a system.

Which OS is more secure?
There is no doubt that Android could currently (depending on the version) be more insecure than iOS due to its openness and high fragmentation. More market share also means more potential targets for attackers and increases the attractiveness for malware development. Nevertheless, with the right policies and precautions, an Android device can be a secure platform and offer a level of security comparable to iOS.
Conclusion: Regardless of the operating system used, a company would do well to consider a BYOD strategy and define appropriate policies and security guidelines for (mobile) end devices.
Compliance Solution Evaluation Security Architecure

